AI-Powered Resilience Command Center
Seamless Integration of Security, Compliance, and GRC Matching the Risk Solution to the Business Need
Strategic Partners










Take Control of your Cyber Defense
Turbo Charged AI Co-Pilot
LEO: Embedded AI Engine enabling risk discovery remediation Role-based Instructive AI : CISO, C-level, IT Analyst, Threat Intel Analyst, Compliance Manager POAM Generation | Code Generation | Presentation & Insight Generation

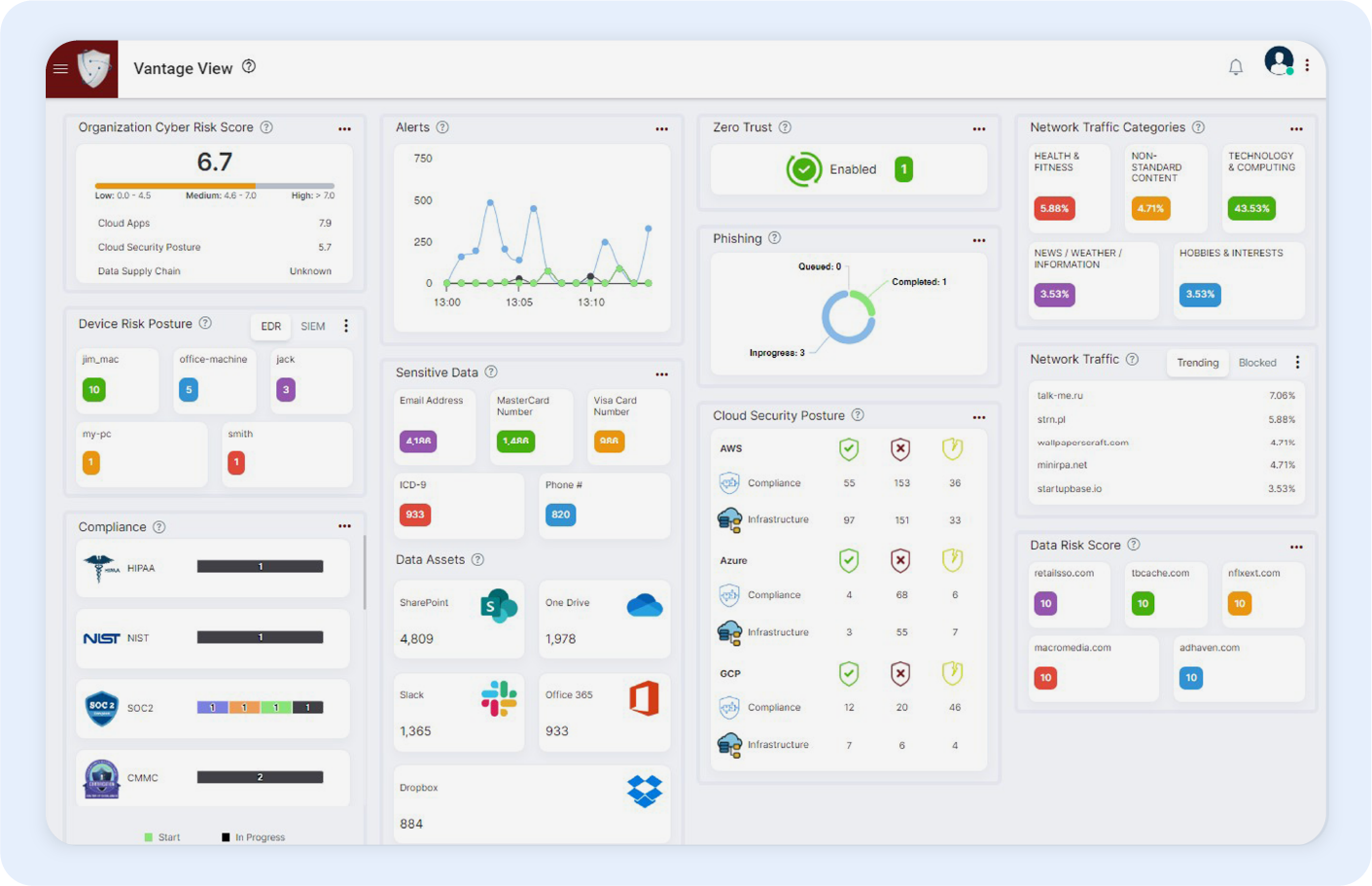
Real-Time Dashboard
Stay ahead with instant insights
Our platform continuously monitors threats, vulnerabilities, and risk exposures across your cloud, network, applications, and endpoints to help you respond faster and stay protected.
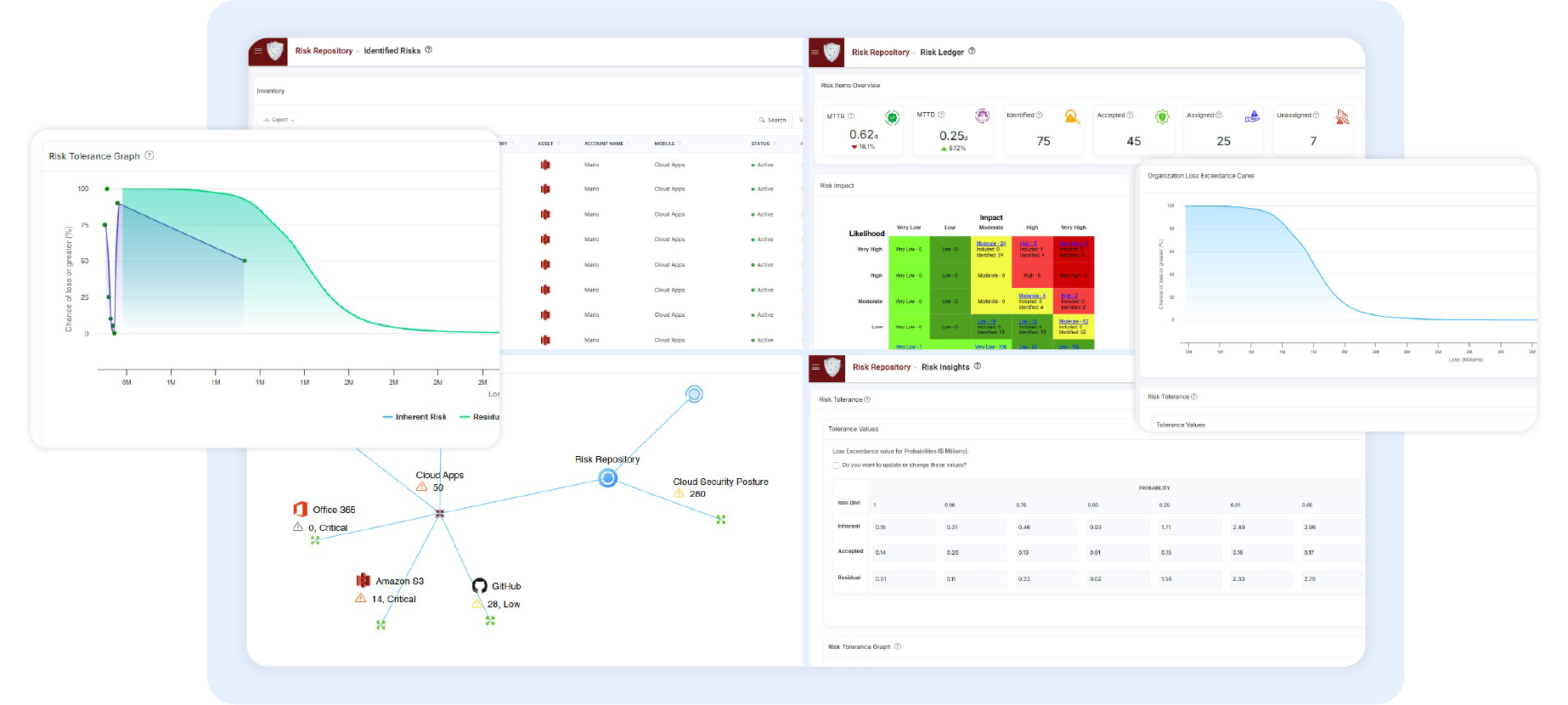
Risk Insights
"Know-Now" Risk Visibility
Threats, risks and vulnerabilities are continuously searched and identified across networks, IT, OT, and IoT devices to identify and mitigate potential threats.

Connect and sync
Over 100+ Integrated Data Partners
Connect seamlessly with over 100+ integrated data partners, including cloud platforms, communication tools, security services, and productivity apps. Cytex ensures smooth synchronization so your workflows stay connected and efficient.

Connect and sync
Over 100+ Integrated Data Partners
Connect seamlessly with over 100+ integrated data partners, including cloud platforms, communication tools, security services, and productivity apps. Cytex ensures smooth synchronization so your workflows stay connected and efficient.
Compliance Automation
Compliance Ops
Continuous compliance automation and monitoring. Integrating regulatory compliance into daily operations.

