AICenturion
Protecting against data exfiltration with the industry's First LLM Firewall with Integrated DLP Securing the use of AI
AICenturion’s proactive, real-time approach acts as a digital immune system ensuring that data doesn’t silently slip outside your organization through LLM interactions. By addressing both external threats and internal vulnerabilities, AICenturion transforms LLMs from a potential liability into a trusted enterprise asset.
Risk Mitigation of LLM Vulnerabilities
- Policy enforcement for different roles and adherence to acceptable use
- Detection of LLM and AI models across the enterprise
- Monitor usage against stated objectives and adjust usage parameters
- Coverage of the OWSAP top LLM vulnerabilities
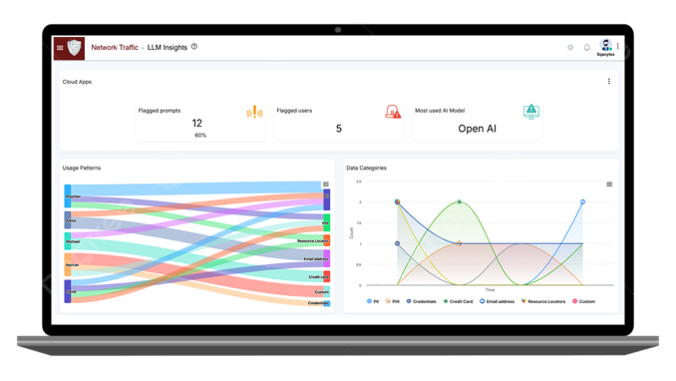
Real-time Data Monitoring & Filtering
Continuously scans inputs and outputs to sanctioned LLMs leveraging DLP policies to detect and classify sensitive data (CUI, PHI, PII) using advanced pattern recognition.
Automated Data Redaction & Blocking
Instantly redacts or blocks sensitive data before it reaches the LLM, ensuring compliance with HIPAA, GDPR, and DoD standards.
Safeguarding Internal AI Tools
Restricts access to sensitive data based on user roles preventing unauthorized internal users from inadvertently exposing confidential information via AI interactions.
Supply Chain Vulnerabilities
Cytex platform’s SBOM and SCAT analysis integrated within the development processes ensure vulnerabilities within the traditional software supply chain and model plugins are identified.
