Unified Resilience Platform
Patent-Pending AI Powered Full Spectrum Cybersecurity
Born out of MIT Research
Cytex was built from the ground up in collaboration with cybersecuity engineers.

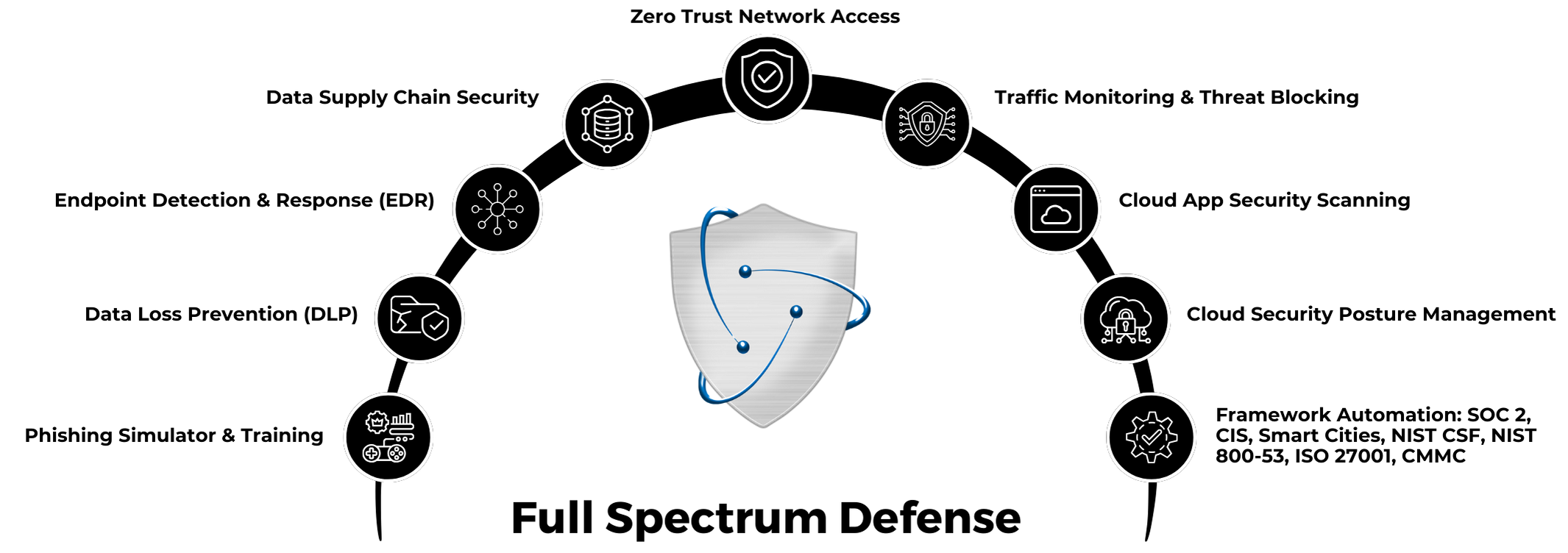
AI Powered Cyber Defense
Network Security
Learn MoreCloud Security
Learn MoreApp Security
Learn MoreDev Sec Ops
Learn MoreCompliance
Learn MoreEDR
Learn MoreData Supply Chain
Learn MoreDevice Management
Learn MoreHRIS Integration
Learn MoreZero Trust
Learn MoreAudify
Learn MorePhishing Simulator
Learn MoreFree Phishing Simulation Software
We believe the digital landscape should be as safe as possible and this specific reason is why we offer our exclusive Phishing Software to you or your business at no cost. This is not a trial offer, the product is full-featured and ready to help your business be safe with email. Complete with training and quick implementation, get started today.